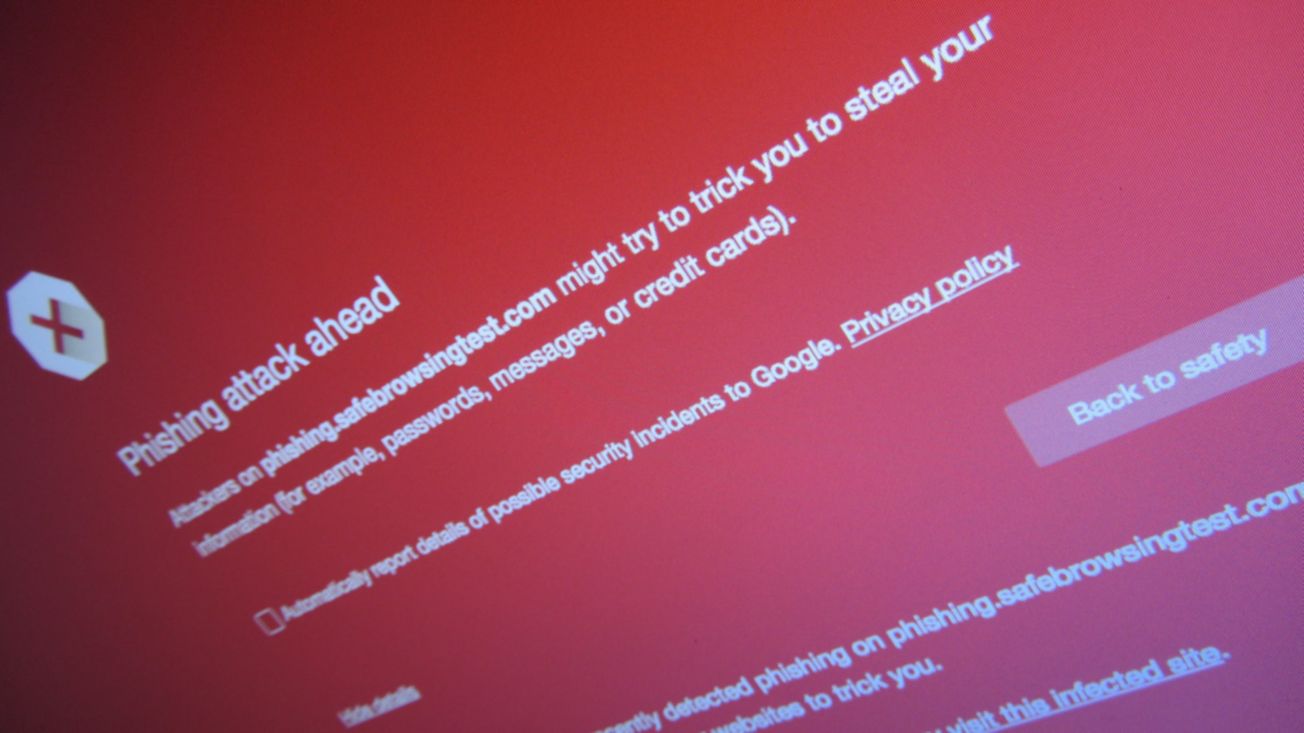
According to a recent report, the newest forms of phishing attacks are the most dangerous ones to date.
Trellix's cybersecurity team has discovered an upgraded form of the callback attack that, if successful, can steal victims' money, encrypt their computers with ransomware, and steal their personal information.
A callback attack is exactly what it sounds like: the scammer calls the victim back to deliver the killing blow over the phone.
Email is used as usual to kick off this particular campaign. A victim is duped into calling a 1-800 number after receiving an email confirmation of a purchase they never made.
Malware, ransomware, and other viruses are typically installed after an attacker has called a target and persuaded them to download remote access software.
The difference is that this campaign goes further. Victims are told the email is spam when they call the number provided because the other person on the other end claims to have checked the database. They then imply the victim's computer has a virus and promise to have a "technical specialist" contact them later in the day.
After the second call, the victim is tricked into downloading bogus antivirus software onto their endpoint, which in turn distributes a ClickOnce executable named support.Client.exe, which in turn installs the ScreenConnect remote access tool.
Trellix explained that an attacker "can also show a fake lock screen and make the system inaccessible to the victim," allowing the attacker to carry out tasks undetected by the victim.
The investigators have uncovered several variations of the campaign, including one that spreads fake cancellation forms through which victims reveal sensitive information. The victims must sign in to their bank account in order to receive the refund. As a result of the scam, they wire funds to the perpetrators.
The victim's screen is locked, a transfer-out request is made, and the screen is unlocked when an OTP (One Time Password) or secondary password is needed, as described by Trellix.
"Victims are duped into thinking they have received their refunds by presenting them with a fake "refund successful" page. To further fool the victim into thinking nothing is amiss, the con artist may send him or her a text message that appears to be from a financial institution confirming the receipt of a fraudulent payment."